V2-EDR EndPoints Information Security Detection and Response
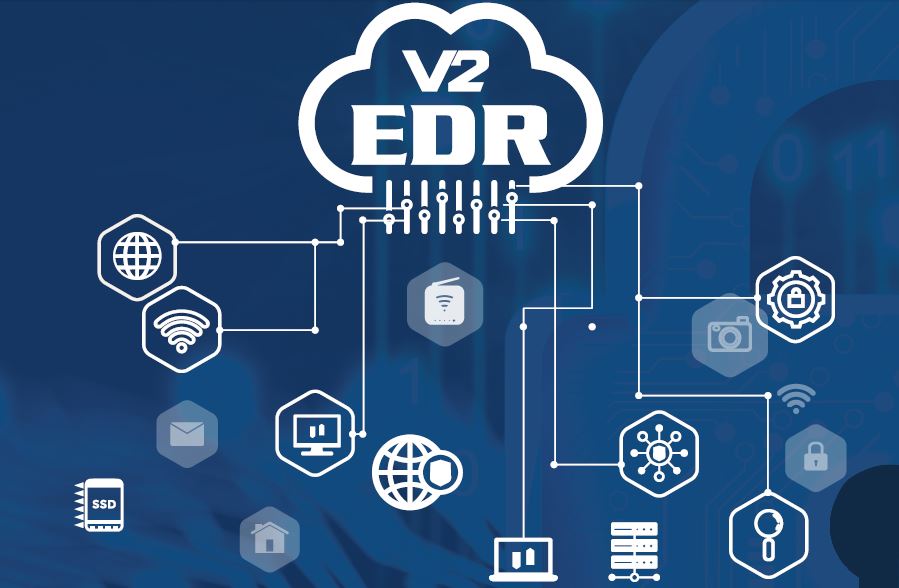
INTRODUCTION
V2-EDR EndPoints Information Security Detection and Response allows you to manage, monitor, detect attacks & malware and provide response mechanisms in order to protect servers, workstations and endPoints. The detection of network attacks, malware as well as processing and response functions are implemented through Agents installed on servers and workstations.
SYSTEM FUNCTION
1. Endpoints Management Function
- Centralized manage system information (Hostname, IP, MAC, Hostfix, ...)
- Manage information security events on centralized multi-platform EndPoints
- Manage security policy enforcement on EndPoints
- Manage access, isolate unsafe EndPoints from the system.
2. Behavior Detection Function
- Detectec network attacks, anomalous behavior of EndPoints based on behavior analysis from system logs.
- Automatically alert, handle, and isolate EndPoints that are detected to have anomalous actions.
- Allows defining, creating rules for analyzing behavior, allowing correlation analysis to detect APT attacks.
3. Malware detection function by evidences
- Malware attacks detection on EndPoints connected to C&C Server
- Malware attacks Detection on EndPoints queried malicious domains
- Malware attacks Detection on EndPoints running malicious apps
- Malware attacks Detection on EndPoints using Yara Rules
- Malware attacks Detection on EndPoints using knowledge base from the TIP system.
4. Response to Information Security Incident Function
- Truy vết, điều tra, phân tích sự kiện, sự cố an toàn thông tin trên EndPoints
- Quản lý tiến trình trên EndPoints
- Quản lý kết nối mạng trên EndPoints
- Quản lý các tiến trình, chương trình hệ thống tự động chạy cùng hệ thống
- Quản lý thông tin các cổng dịch vụ trên EndPoints
- Quản lý thông tin đăng nhập hệ thống trên EndPoints
- Quản lý thông tin truy cập, tải dữ liệu trên EndPoints
- Tải tệp tin về máy chủ EDR, phân tích, quét mã độc, gửi thông tin lên Sandbox
- Tracing, investigating, analyzing information security events and incidents on EndPoints
- Manage progress on EndPoints
- Manage network connections on EndPoints
- Manage processes, system programs that automatically run with the system
- Information management of service portals on EndPoints
- Manage system login information on EndPoints
- Manage access information, download data on EndPoints
- Download files to EDR server, analyze, scan for malware, send information to Sandbox
5. Incidents Investigation and Analysis
- Allow deep log analysis for each information field
- Allow writing correlation rules to detect and investigate attacks and incidents
- Enable incident analysis and investigation through an intuitive interface.
6. System administration function
- The Dashboard function allows administrators to have an overview of the system.
- The Behavior Blocking function manages behavioral attack detection and prevention alerts.
- The report generation function allows administrators to create customized reports for each specific condition in different formats.
- System configuration management
- Manage system administrator accounts
- Manage system software updates from the Cloud
- System status information
- Manage Logs of activity on the system
- System administration through Console and SSH
SERVICE PACKAGES
|
FUCTION
|
EDR BASIC
|
EDR ADVANCE
|
EDR PRO
|
EDR PRO+
|
|
Multi-platform EndPoints Information Management
|
X
|
X
|
X
|
Custom
|
|
Detect Malware by Evidences
|
X
|
X
|
X
|
Custom
|
|
Interactive Troubleshooting on EndPoints
|
X
|
X
|
X
|
Custom
|
|
Detect Malware by Behavior
|
|
X
|
X
|
Custom
|
|
Incidents Investigation and Analysis
|
|
X
|
X
|
Custom
|
|
EndPoints' Network Access Policy Management
|
|
|
X
|
Custom
|
SUPPORT IMPLEMENT ON
- Windows 11; Windows 10
- Windows Server 2008 R2;
- Windows Server 2012 R2;
- Windows Server 2016;
- Windows Server 2019
- CentOS 7.x; CentOS 8.x
- Debian 10; Debian 11