V2-WAF Web Application Firewall System
.JPG)
INTRODUCTION
V2-WAF Web Application Firewall System is a solution to protect web applications against network attacks. WAF is distributed as a device (hardware) or software (license) installed on server, which monitors the information using the http/https protocol between the user's browser and the web server. WAF enforces security policies based on attack signatures, standard protocols, and anomalous web application traffic.
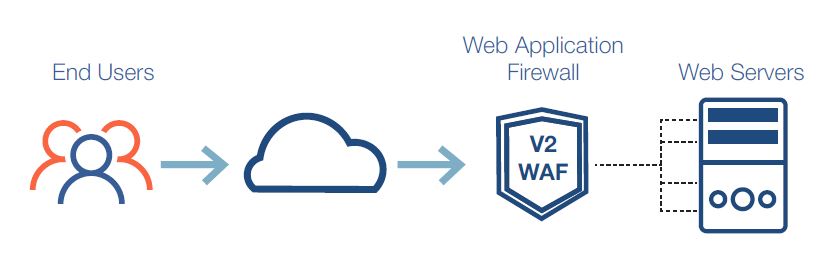
SYSTEM FUNCTION
1. Web Application Security
- Filter Information packages by blacklist
- IP Adress Filtering
- Dissolution IP address into geographic coordinates
- Áp dụng Top 10 của OWASP
- CSS attack prevention
- SQLi attack prevention
- CSRF attack prevention
- Session Hijacking attack prevention
- Intergrate vulnerability scanning feature
- Malware Dectection
- Virtual patching
- Prevent Brute Force attack
- Syntax-based SQLi attack detection
- Stateful firewall intergation at floor 4th
- DoS/DdoS attack prevention
- Web Defacement attack prevention
2. Processing and correlation analysis - Behavior Detection
- Allows you to set up rules to automatically correlate various log sources to detect network attacks.
- Allows detection of anomalous behavior to accurately detect attackers and attacked objects based on the ability to automatically analyze warnings received from the system.
- Allows the administrator to set up a set of rules to detect anomalous user behavior and abnormal network connections on the system.
.JPG)
3. Alerts and automatically prevents attacks
- Automated attack alerts via SMS, Email...
- The system provides interoperability with network devices (Cisco Router – Juniper, Firewall Cisco PIX – ASA, Firewall Check-Point, Firewall Fortinet...), Security devices (Firewall, NAC, IDS, IPS) and operating systems (Windows Server 2008, 2012, Linux Centos, Fedora, Ubuntu, Debian, Linux Transparent Firewall ...) to perform network attack prevention.
- This capability allows the system to prevent network attacks without affecting the operation and performance of the system and does not require installing Agents on devices or servers.
4. Incidents nvestigation and analysis
- Allows deep log analysis for each information wall.
- Allows writing correlation rules and allows detection and investigation of attacks and incidents.
- Enables incident analysis and investigation through an intuitive interface.
5. System management function
- The Dashboard function allows administrators to have an overview of the system.
The Behavior Blocking function manages behavioral attack detection and prevention alerts.
The report generation function allows administrators to create customized reports according to specific conditions and different formats.
System configuration management
Manage system administrator accounts
Manage system software updates from the Cloud
System status information
Manage activity logs on the system
System administration through Console and SSH
6. Minimum processing capacity
- Throughput: 200 Mbps
- Backend Servers Supported: 10-25
- HTTP Transactions Per Second: 30,000
- HTTP Connections Per Second: 10,000
- HTTPS Transactions Per Second: 12,000
- Concurrent Connections: 500,000
SERVICE PACKAGES
|
FUNCTION
|
WAF BASIC
|
WAF ADVANCE
|
WAF PRO
|
WAF PRO+
|
|
Prevent various types of attacks as Top 10 OWASP
|
X
|
X
|
X
|
Custom
|
| Prevent 1day attack using Virtual Patching |
X |
X |
X |
-load-Custom |
|
Hot Stand By Load-balancing
|
|
X
|
X
|
Custom
|
|
Manage attacj resource by BlackList
|
|
X
|
X
|
Custom
|
|
Network attack prevent by behavior
|
|
X
|
X
|
Custom
|
|
Prevent pplication layer DDoS attack
|
|
|
X
|
Custom
|
IMPLEMENTATION PLAN
- Implementing as a reverse proxy
- Implementing as a transparent proxy
- Implementing under the mechanism of offline sniffing
- Implementing with the Web Cache Communication Protocol